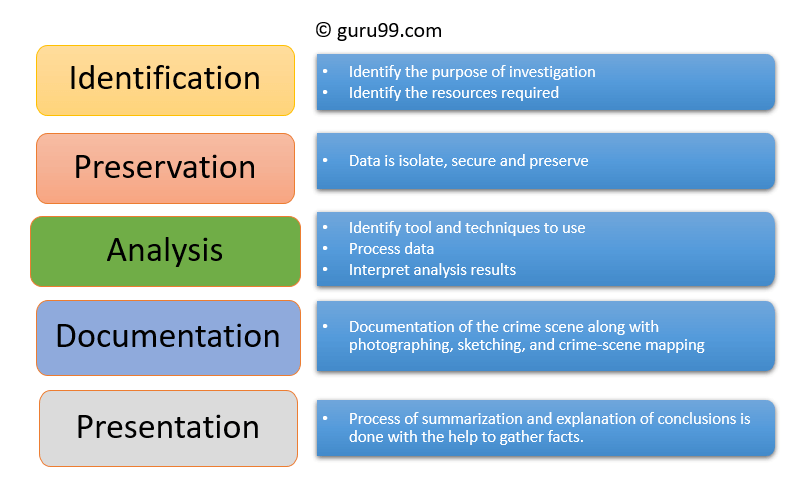
Identify Two Phases of the Access Control Process
To accomplish that we need to follow three steps. The steps involved in the control process are-1.

Types Of Data Abstraction In Dbms Physical Logical View Data Link Layer Data Structures Dbms
Installer needs to familiarize with the site and identify the routes used by existing cables and services.

. To assure the safety of an access control system it is essential to. Self-Service Role Matrix and Rights Management Phase 6. Ii Activities of users with significant information system roles and responsibilities are.
When a user logs on the system authenticates the users account name and password. 4 Steps of Control Process are. Check to see whether it may be possible.
There are two basic parts of the access control model. This is because the main aim of controlling is to direct a businesss actions towards its goals. The rules for a large access control project are designed so that you your customer their support people other contractors and engineers and the municipality are all on the same page.
Periodic evaluation of completed action to date. The attacker seeks to identify and gain the necessary level of privilege to achieve their objectives. If the logon is successful the system creates an access.
Identification and authorization Selected Answer. They have control over access channels and credentials acquired in the previous phases. Accumulation classification and recording of this information.
THE 10 PHASES OF IDENTITY AND ACCESS MANAGEMENT The 10 Phases of Identity and Access Management Phase 1. An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. During which phase of the access control process does the system answer the question What can the requestor access A.
Problem analysis phase 4. For example feedback control would involve evaluating a teams progress by comparing the production standard to the actual production output. Security descriptors which contain the security information that protects a securable object.
Davis identifies four phases in the comparison. Password Policy Enforcement Phase 3. Finally the attacker gains access to the target data.
Password Management Phase 2. The four steps in the control process are. Enterprise Reduced Single Sign-On SSO.
Proactive control anticipates future implications. User Provisioning Phase 5. Establishing standards and methods for measuring performance.
56 Which of the following phases identifies and expresses requirements prioritizes requirements updates project plan and communications the requirements statement. Ed wants to make sure that his system is designed in. At the third phase deviations if any are noted between standards and performance.
Question 12 0 out of 2 points Identify two phases of the access control process. Educators go through a rigorous application process and every answer they submit is reviewed by our in-house editorial team. The weakest identification capabilities will.
Authorization is the third step of access control. Knowledge and Ownership and characteristics Identification Methods - The first step enforcing an authorization policy in Identification. Concurrent control concerns the present.
Access control models include Mandatory Access Control MAC Role Based Access Control RBAC Discretionary Access Control DAC and Rule-Based Access Control RBAC which define the level of. The control process is the functional process for organizational control that arises from the goals and strategic plans of the organization. Mail servers document management systems and customer data are compromised.
Decisions analysis phase 3. Response within two seconds of the valid completion of the necessary. Feedback control concerns the past.
The task of fixing goals and standards takes place while planning but it plays a big role in controlling also. Establishment of Standards 2. A state of access control is said to be safe if no permission can be leaked to an unauthorized or uninvited principal.
Analysis of Deviations 5. Every project will have two types of standards. Logical design phase 2.
Access control systems grants access to resources only to users whose identity has been proved and having the required permissions. Identify two phases of the access control process. Also without control you will not be able to actionable lead the workforce.
Identify two phases of the access control Process. For access control to be effective it must provide some way to identify an individual. Reporting the status of accomplishment to higher line authority.
Access control is paramount for security and fatal for. Measurement of Performance 3. While the control process is flexible and looks different for every project and manager.
Any major project evolves from the same basic phases. You log onto a network and are asked to present a combination of elements such as user name password token smart card or biometrics. Establishing Standards and.
Comparison of Actual and Standard Performance 4. During this phase the manager can identify gaps between the standards and. This is an example of which of the following.
The control process consists of the following basic elements and steps. I System accounts and access are reviewed at least monthly to ensure that. 4 stages involved in installation process of electronic access control system.
1 Only the appropriate levels of access are allowed 2 Access is granted only to authorized personnel and 3 Users access rights are limited to least privilege. Access tokens which contain information about a logged-on user. Linked to identification methods -.
Establishing goals and standards. User De-Provisioning Phase 4. Receiving the raw data.
Feedback occurs after an activity or process is completed.

Access Control Software From Xlnc Io Software Software Sales Access Control
Comments
Post a Comment